Navigating HIPAA Space: Protecting Your Health Data In A Digital World
In an increasingly interconnected world, where personal information flows freely across digital channels, the protection of sensitive health data has become paramount. This is precisely where the concept of "HIPAA space" emerges as a critical framework, defining the boundaries and safeguards necessary to ensure the privacy and security of health information. From the moment the Health Insurance Portability and Accountability Act (HIPAA) was enacted in 1996, its primary objective has been clear: to improve the efficiency and effectiveness of the health care system by establishing federal standards protecting sensitive health information from disclosure without proper authorization.
The implications of HIPAA extend far beyond mere paperwork; they permeate every facet of healthcare operations, influencing how patient data is collected, stored, transmitted, and accessed. Understanding what constitutes a secure "HIPAA space" is no longer just the responsibility of healthcare providers but also of anyone who interacts with health information, including patients themselves. This comprehensive guide will delve into the multifaceted nature of HIPAA, exploring its foundational principles, practical applications in various environments, and the crucial role it plays in safeguarding your most personal health details.
Table of Contents
- What is HIPAA and Why it Matters?
- Defining "HIPAA Space": More Than Just a Room
- Building a HIPAA Compliant Home Office
- HIPAA's Flexibility and Scalability
- Understanding Your HIPAA Rights as a Patient
- The Role of Technology: HIPAAspace Web Services
- Enforcement and Penalties: What Happens When Rules Are Broken?
- Staying Informed: Resources for Compliance
What is HIPAA and Why it Matters?
At its core, the Health Insurance Portability and Accountability Act of 1996 (HIPAA) is a landmark federal law designed to protect sensitive patient health information. Enacted as Public Law 104-191, its initial aim was to improve the efficiency and effectiveness of the healthcare system by standardizing electronic healthcare transactions. However, its most significant and widely recognized impact lies in its provisions for safeguarding patient privacy and security. The US Health Insurance Portability and Accountability Act (HIPAA), enacted in 1996, was established to safeguard patient privacy and ensure the confidentiality of medical records.
Before HIPAA, there was no national standard for protecting health information, leaving patient data vulnerable to misuse and unauthorized disclosure. This created a patchwork of state laws that often provided inconsistent or insufficient protections. The absence of a unified framework meant that sensitive health details could be shared without a patient's knowledge or consent, leading to potential discrimination, identity theft, or simply a profound breach of trust.
The Genesis of HIPAA
The journey to HIPAA began with a clear recognition of the need for federal oversight in healthcare data management. The Act was born out of a desire to address several critical issues:
- Portability: Ensuring that individuals could maintain health insurance coverage when changing jobs.
- Accountability: Holding healthcare providers and related entities accountable for the protection of patient data.
- Administrative Simplification: Streamlining healthcare operations through standardized electronic transactions, which inherently required robust security measures.
From this foundation, HIPAA evolved to become the comprehensive privacy and security framework we know today. It established federal standards protecting sensitive health information from disclosure without proper authorization, fundamentally changing how healthcare entities handle patient data.
Key Pillars: Privacy and Security
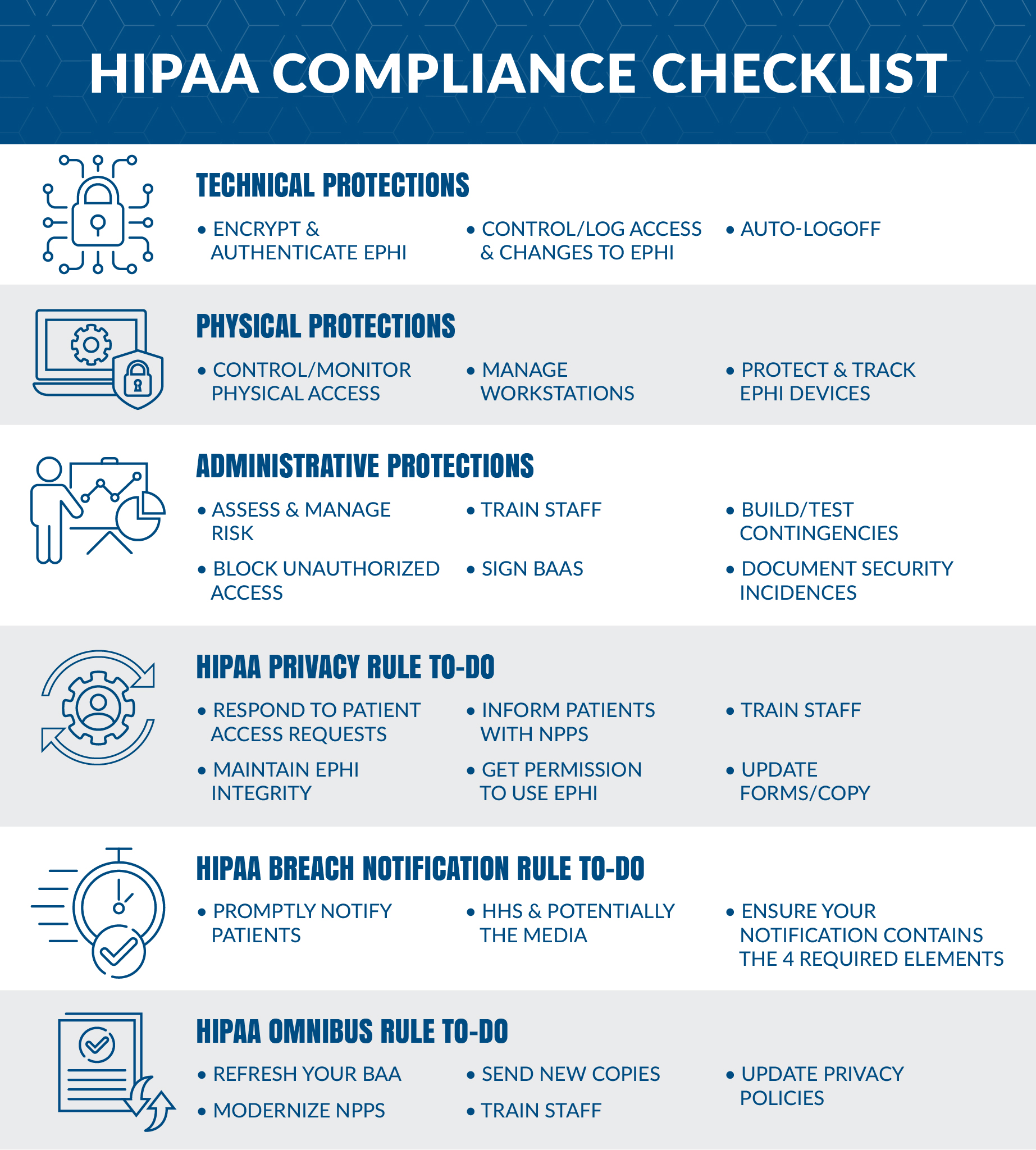
HIPAA is often discussed in terms of its two main rules: the Privacy Rule and the Security Rule. Both are integral to creating a secure "HIPAA space" for health information.
- The Privacy Rule: This rule sets national standards for the protection of individually identifiable health information (PHI) by covered entities and their business associates. It gives patients significant rights over their health information, including the right to access their medical records, request corrections, and know who has accessed their information. It dictates when and how PHI can be used and disclosed.
- The Security Rule: This rule complements the Privacy Rule by addressing the technical and non-technical safeguards that covered entities must put in place to protect electronic protected health information (ePHI). This is a summary of key elements of the Health Insurance Portability and Accountability Act of 1996 (HIPAA) Security Rule, as amended by the Health Information Technology for Economic and Clinical Health (HITECH) Act. It mandates administrative, physical, and technical safeguards to ensure the confidentiality, integrity, and availability of ePHI.
Together, these rules form the backbone of HIPAA compliance, ensuring that whether information is on paper or in digital format, it remains protected.
Defining "HIPAA Space": More Than Just a Room
The term "HIPAA space" might conjure images of secure data centers or locked filing cabinets, and while those are certainly components, the concept is far broader. A "HIPAA space" refers to any environment, physical or digital, where Protected Health Information (PHI) is created, stored, transmitted, or accessed, and where the necessary safeguards are in place to ensure its confidentiality, integrity, and availability as mandated by HIPAA regulations. It's not merely a physical location but a state of compliance that permeates an entire operational ecosystem.
Understanding this broad definition is crucial because HIPAA isn’t just about paperwork and digital records; it may have a significant impact on how organizations operate and how individuals interact with their health data. It encompasses everything from a doctor's office to a cloud server, and even a remote worker's home office.
Physical HIPAA Space
A physical HIPAA space refers to any tangible location where PHI is handled. This includes:
- Healthcare Facilities: Hospitals, clinics, doctor's offices, pharmacies, and laboratories. These environments must implement physical safeguards such as restricted access to areas where PHI is stored (e.g., server rooms, medical records departments), locked filing cabinets, and secure disposal methods for paper records.
- Administrative Offices: Even offices that don't directly provide patient care but handle billing, scheduling, or other administrative tasks involving PHI must maintain a secure physical HIPAA space. This includes secure workstations, clear desk policies, and controlled access to office premises.
- Shared Office Environments: As you set up your shared office space, it's essential to prioritize HIPAA compliance to protect sensitive patient information. This means ensuring that PHI is not visible to unauthorized individuals, that conversations about patient data are not overheard, and that physical documents are secured when not in use.
The key principle here is limiting physical access to PHI only to authorized personnel and protecting it from environmental hazards like fire or water damage.
Digital HIPAA Space
In today's digital age, the digital HIPAA space is arguably more complex and expansive. It encompasses all electronic systems and networks where ePHI resides or is transmitted. This includes:
- Electronic Health Record (EHR) Systems: These are the central repositories for patient data and must be secured with robust access controls, encryption, and audit trails.
- Email and Communication Platforms: Any email or messaging system used to transmit PHI must be encrypted and secure. The general rule of thumb is to share sensitive information only on official, secure websites or platforms designed for healthcare communication.
- Cloud Storage and Servers: Many healthcare entities use cloud services for data storage. These services must be HIPAA compliant, requiring a Business Associate Agreement (BAA) with the cloud provider to ensure they adhere to HIPAA's security standards.
- Network Infrastructure: Firewalls, intrusion detection systems, and secure network configurations are vital to protect ePHI from cyber threats.
- Mobile Devices: Laptops, tablets, and smartphones used by healthcare professionals must be secured with strong passwords, encryption, and remote wipe capabilities in case of loss or theft.
The digital HIPAA space requires continuous vigilance, regular security assessments, and prompt responses to potential breaches to maintain compliance.
Building a HIPAA Compliant Home Office
With the rise of remote work, the home office has become an increasingly important "HIPAA space" for many healthcare professionals and their support staff. A HIPAA compliant home office is a working environment set up to support HIPAA compliance and safeguard the privacy and security of Protected Health Information (PHI). This isn't just a suggestion; for covered entities and business associates, it's a regulatory necessity. As Steve Alder noted on April 22, 2025, setting up such an environment requires careful consideration.
To ensure a home office meets HIPAA standards, several measures must be implemented:
- Physical Security:
- Dedicated Workspace: If possible, a dedicated room or area where PHI is handled, with a lockable door to prevent unauthorized access by family members or visitors.
- Secure Storage: All physical documents containing PHI must be stored in locked cabinets or drawers when not in use.
- Shredding: A cross-cut shredder for disposing of any paper documents containing PHI.
- Privacy Screens: Use privacy screens on monitors to prevent "shoulder surfing" by others in the household.
- Technical Security:
- Secure Network: A strong, password-protected Wi-Fi network (WPA2 or WPA3 encryption) separate from any guest networks. Consider a VPN (Virtual Private Network) for secure access to organizational systems.
- Encrypted Devices: All computers, laptops, and external storage devices used for PHI must be encrypted.
- Strong Passwords and Multi-Factor Authentication (MFA): Implement complex, unique passwords for all systems and accounts, and enable MFA wherever possible.
- Up-to-date Software: Ensure operating systems, antivirus software, and all applications are regularly updated to patch security vulnerabilities.
- Firewall Protection: Both hardware and software firewalls should be active on all devices.
- Administrative Safeguards:
- Training: Regular HIPAA training for remote employees to ensure they understand their responsibilities.
- Access Controls: Employees should only have access to the minimum necessary PHI required for their job functions.
- Incident Response Plan: A clear plan for what to do in case of a security incident or breach in the home office.
- No Personal Use of Work Devices: Discourage or prohibit the use of work devices for personal activities to reduce the risk of malware or data exposure.
Creating a HIPAA compliant home office is an ongoing process that requires diligence and adherence to established protocols. It’s about extending the secure "HIPAA space" from the traditional office environment into the remote workspace.
HIPAA's Flexibility and Scalability
One of the remarkable aspects of HIPAA, often overlooked, is its inherent flexibility and scalability. The HIPAA rules are flexible and scalable to accommodate the enormous range in types and sizes of entities that must comply with them. This means that there is no single, one-size-fits-all solution for compliance. Instead, the regulations provide a framework that allows organizations to implement safeguards appropriate to their specific circumstances, considering factors like their size, complexity, technical infrastructure, and the nature of the PHI they handle.
For instance, a small, independent physician's office will have different resources and needs compared to a large, multi-state hospital system. HIPAA acknowledges this disparity. While both must comply with the core principles of privacy and security, the specific administrative, physical, and technical safeguards they implement can vary. A small practice might rely on off-the-shelf encrypted communication tools, while a large hospital might develop custom, highly sophisticated security architectures.
This flexibility is crucial for several reasons:
- Adaptability to Technology: Healthcare technology evolves rapidly. A rigid set of rules would quickly become outdated. HIPAA's flexibility allows organizations to adopt new technologies (like cloud computing or telemedicine platforms) while still maintaining compliance, as long as the underlying security principles are met.
- Cost-Effectiveness: It prevents undue financial burden on smaller entities. Requiring a small clinic to implement the same enterprise-level security solutions as a major hospital would be impractical and potentially prohibitive.
- Risk-Based Approach: HIPAA encourages a risk-based approach to security. Covered entities are required to conduct a risk analysis to identify potential threats and vulnerabilities to ePHI. Based on this analysis, they must implement reasonable and appropriate safeguards to mitigate those risks. This ensures that resources are allocated effectively to protect the most vulnerable areas.
This scalability means that establishing a robust "HIPAA space" is achievable for any entity, regardless of its size, provided it undertakes a thorough assessment of its specific risks and implements safeguards commensurate with those risks.
Understanding Your HIPAA Rights as a Patient
While much of the discussion around HIPAA focuses on the responsibilities of healthcare entities, it's equally important for individuals to understand their rights. Patients and health care consumers can learn about their rights under HIPAA, which include privacy, security, and the ability to access their health information. These rights empower individuals to have greater control over their personal health data and ensure that it is used and disclosed appropriately.
The Office for Civil Rights (OCR), which enforces HIPAA, has teamed up with the HHS Office of the National Coordinator for Health IT to create "Your Health Information, Your Rights!", a series of educational materials and videos, including "HIPAA Right of Access videos," to help patients understand these crucial protections.
Key patient rights under HIPAA include:
- The Right to Access Your Health Information: You have the right to inspect and obtain a copy of your medical and billing records. This includes electronic records. Covered entities must provide this information within 30 days (with a possible 30-day extension) and can only charge a reasonable, cost-based fee.
- The Right to Request an Amendment: If you believe your health information is inaccurate or incomplete, you have the right to request that a covered entity amend it.
- The Right to an Accounting of Disclosures: You can request a list of certain disclosures of your health information made by a covered entity.
- The Right to Request Restrictions: You can ask your healthcare provider to limit how your information is used or shared, though the provider is not always required to agree. However, if you pay for a service or health care item out-of-pocket in full, you can ask your provider not to tell your health plan about it.
- The Right to Request Confidential Communications: You have the right to request that your healthcare provider communicate with you about medical matters in a certain way or at a certain location (e.g., calling your cell phone instead of your home phone, or sending mail to a P.O. box).
- The Right to Receive a Notice of Privacy Practices: Covered entities must provide you with a notice that explains how they may use and share your health information and outlines your rights.
- The Right to File a Complaint: If you believe your HIPAA rights have been violated, you have the right to file a complaint with the covered entity or directly with the OCR.
Understanding and exercising these rights is a vital part of maintaining your personal "HIPAA space" and ensuring your health data is handled responsibly.
The Role of Technology: HIPAAspace Web Services
In the complex landscape of healthcare data, technology plays an indispensable role in facilitating compliance and managing vast amounts of information. This is where entities like HIPAAspace come into play, offering specialized web services designed to assist healthcare organizations in navigating the intricacies of HIPAA regulations. HIPAAspace is an unfunded company based in San Diego (United States), founded in 1996, operating as a healthcare data provider. While it has not raised any funding yet, its services are crucial for various compliance needs.
HIPAAspace web services provide tools and resources that streamline operations and ensure data integrity within the "HIPAA space." These services often include:
- NPI Lookup: The National Provider Identifier (NPI) is a unique 10-digit identification number issued to healthcare providers in the United States. NPI lookup services allow organizations to verify provider identities, which is essential for accurate billing and claims processing, ensuring that interactions occur with legitimate and recognized entities.
- HCPCS Lookup: The Healthcare Common Procedure Coding System (HCPCS) is a collection of standardized codes that represent medical procedures, services, and supplies. HCPCS lookup tools assist in accurate medical coding, which is critical for proper reimbursement and maintaining compliance with billing regulations.
- NDC Lookup: National Drug Code (NDC) is a unique 10-digit, 3-segment number assigned to each medication listed under the U.S. Food and Drug Administration (FDA). NDC lookup services are vital for pharmacies, prescribers, and insurers to identify drugs accurately, manage inventories, and process claims.
- HIPAA Validation: This service ensures that data formats and transactions comply with HIPAA standards, particularly for electronic data interchange (EDI). It helps prevent errors in claims submission, eligibility checks, and other administrative transactions, thereby improving efficiency and reducing rejections.
The availability of such major HIPAA codelists for lookup, using HIPAAspace web services, underscores the importance of standardized data in maintaining an efficient and compliant healthcare system. These technological tools are not just about convenience; they are fundamental to creating a reliable and secure "HIPAA space" where data flows accurately and securely between various healthcare stakeholders. With professionals from all over the industry, and engineers on standby 24x7, such services aim to provide robust support for healthcare data management.
Enforcement and Penalties: What Happens When Rules Are Broken?
The strength of HIPAA lies not just in its comprehensive rules but also in its enforcement mechanisms. When covered entities or business associates fail to comply with HIPAA regulations, they can face significant penalties. The Office for Civil Rights (OCR) within the U.S. Department of Health and Human Services (HHS) is responsible for enforcing the HIPAA Privacy, Security, and Breach Notification Rules. Their investigations can result in corrective actions and monetary fines, emphasizing the serious nature of maintaining a secure "HIPAA space."
Penalties for HIPAA violations are tiered and depend on the level of culpability:
- Tier 1: Unknowing Violation: The covered entity did not know and, by exercising reasonable diligence, would not have known that a violation occurred. Minimum penalty: $127 per violation, up to $31,940 for identical violations per calendar year.
- Tier 2: Reasonable Cause: The violation was due to reasonable cause and not willful neglect. Minimum penalty: $1,278 per violation, up to $63,948 for identical violations per calendar year.
- Tier 3: Willful Neglect (Corrected): The violation was due to willful neglect, but the covered entity corrected the violation within 30 days. Minimum penalty: $12,781 per violation, up to $255,551 for identical violations per calendar year.
- Tier 4: Willful Neglect (Not Corrected): The violation was due to willful neglect and was not corrected within 30 days. Minimum penalty: $63,948 per violation, up to $1,918,179 for identical violations per calendar year.
It's important to note that a penalty will not be imposed for violations in certain circumstances, such as if the violation was due to a criminal act by another person (and the entity was not negligent) or if the entity can demonstrate that it took reasonable steps to prevent the violation. However, these exceptions are rare and require substantial proof of due diligence.
Beyond monetary fines, violations can lead to reputational damage, loss of patient trust, and even criminal charges in cases of egregious willful neglect. This underscores why proactive measures to establish and maintain a secure "HIPAA space" are not just regulatory requirements but fundamental to ethical healthcare practice.
Staying Informed: Resources for Compliance
The landscape of healthcare data privacy and security is constantly evolving, with new technologies, threats, and interpretations of regulations emerging regularly. For anyone involved in healthcare, from providers and administrators to patients, staying informed about HIPAA is crucial. The journey to maintaining a robust "HIPAA space" is ongoing, requiring continuous learning and adaptation.
Fortunately, there are numerous reliable resources available to help individuals and organizations understand and comply with HIPAA:
- Official HHS.gov Resources: The U.S. Department of Health & Human Services (HHS) website is the authoritative source for HIPAA information. In this section, you will find educational materials to help you learn more about the HIPAA Security Rule and other sources of standards for privacy and security. This includes detailed guidance, FAQs, and enforcement actions.
- Office for Civil Rights (OCR): As the primary enforcement agency, the OCR's website provides comprehensive information on patient rights, breach notifications, and how to file a complaint. Their "Your Health Information, Your Rights!" series is particularly valuable for patients.
- National Institute of Standards and Technology (NIST): NIST develops cybersecurity frameworks and guidelines that are often referenced by HIPAA. Their publications offer technical guidance on implementing security controls.
- Professional Associations: Organizations like the American Medical Association (AMA), American Hospital Association (AHA), and HIMSS (Healthcare Information and Management Systems Society) provide resources, training, and advocacy related to HIPAA compliance for their members.
- Industry Publications and Webinars: Many reputable healthcare IT and legal publications offer up-to-date analysis and advice on HIPAA. Attending webinars and conferences can also provide valuable insights and networking opportunities.
Engaging with these resources helps ensure that practices, policies, and technologies remain aligned with current HIPAA requirements, safeguarding patient data effectively and maintaining the integrity of the entire "HIPAA space."
Conclusion
The concept of "HIPAA space" transcends mere physical boundaries; it represents a comprehensive commitment to safeguarding sensitive health information in every environment where it exists. From the foundational principles laid out by the Health Insurance Portability and Accountability Act of 1996 to the intricate technical safeguards required for digital data, HIPAA ensures that patient privacy and data security remain paramount. We've explored how this critical legislation shapes everything from traditional healthcare settings to the modern remote work environment, emphasizing the need for a HIPAA compliant home office and the inherent flexibility of the rules to accommodate diverse entities.
Understanding your rights as a patient under HIPAA is just as crucial as understanding the responsibilities of covered entities. The availability of technological tools, such as HIPAAspace web services for NPI, HCPCS, and NDC lookups, further underscores the industry's dedication to efficient and secure data management. Ultimately, maintaining a secure "HIPAA space" is not just about avoiding penalties; it's about fostering trust, ensuring ethical data handling, and protecting the deeply personal health

Hipaa Space HIPAA Technical Safeguards - Protecting Sensitive Data

Hipaa Space
What Is HIPAA Compliance? Checklist & Guide 2024